Security.Desk
Überwacht zuverlässig die Hardware-Schnittstellen Ihrer Clients,
kontrolliert mobile Speicher und verhindert effektiv unerlaubten Datentransfer.
Maximale, granulare IT-Sicherheit
Die USB- und Endpoint-Security-Lösung Security.Desk hilft, externe Hardwareschnittstellen dauerhaft abzusichern, überwacht mobile Speicher und Internet-Protokolle und unterstützt Sie dabei, Sicherheitslücken erfolgreich zu schließen.
- Schützt
- Erkennt
- Überwacht
Dabei geht das Tool weit über die Möglichkeiten von Add-Ons gängiger Virenschutzlösungen oder Bordmittel der Hersteller hinaus.






Schützt
Schützt Daten und Netzwerke vor
Datendiebstahl oder dem Einschleppen
von Viren und Trojanern über Wechseldatenträger.
Erkennt
Erkennt automatisch, wenn ein Flash-Speicher, ein Smartphone oder eine Digitalkamera über USB oder FireWire an einen PC angeschlossen oder eine CD oder SD-Speicherkarte eingelegt wird und überwacht sämtliche Hardware-Schnittstellen und Internet-Protokolle am Endgerät.
Überwacht
Auch mobile Speicher an Thin Clients in Windows Terminal Server- oder CITRIX-Umgebungen lassen sich überwachen
Führend in der granularen Absicherung:
Zudem unterstützt Sie Security.Desk dabei, indem die Lösung:
- unkontrollierten Datenabfluss verhindert,
- Dateibewegungen protokolliert,
- Dateien für Dritte unlesbar macht,
- die Ausführung unerwünschter Programme verhindert oder
- das Eindringen externer Gefahren nicht möglich macht.
Security.Desk Module:
Nur zahlen, was man wirklich braucht!
Erwerben Sie nur die Module, die tatsächlich für Ihre Bedürfnisse relevant sind. Ob Sie ein einzelnes Modul oder mehrere nutzen möchten – gestalten Sie Ihre Lösung flexibel nach Maß. Weitere Module können bei Bedarf jederzeit ergänzt werden.
Terminal Server
Überwachung und Kontrolle von Dateitransfers über Terminal-Server
Netzwerkprotokoll
Überwachung und Aufzeichnung von Dateiübertragungen über Internet-Protokolle
Active Directory Integration
Automatisierte Übernahme von Geräten aus dem AD

Security.Desk: Kontrolle von mobilen Speichern und Hardware-Schnittstellen
Security.Desk ermöglicht die umfassende Kontrolle über mobile Speichergeräte wie Smartphones, Digitalkameras und mehr, die an den PCs Ihres Netzwerks genutzt werden.
- Überwachung aller Schnittstellen: Die Software kontrolliert alle Hardware-Schnittstellen und Internet-Protokolle (z. B. http, ftp) am Endgerät.
- Automatische Erkennung: Geräte wie Flash-Speicher, die über USB oder FireWire angeschlossen werden, sowie eingelegte CDs oder SD-Karten, werden automatisch erkannt.
- Flexible Steuerung: Legen Sie fest, ob der Datentransfer blockiert oder nur eingeschränkt gestattet wird. Alle Dateibewegungen können dabei protokolliert werden.
- Dateiprotokolle helfen dabei, nachzuvollziehen, welcher Mitarbeiter an einem PC Daten mit einem mobilen Speicher ausgetauscht hat.
- Die Kontrolle kann bis auf die Ebene der erlaubten Dateien und Dateitypen heruntergebrochen werden.
- Das Reporting gibt einen aktuellen Überblick über den Einsatz externer Speichermedien pro Benutzer und Rechner im Netzwerk.
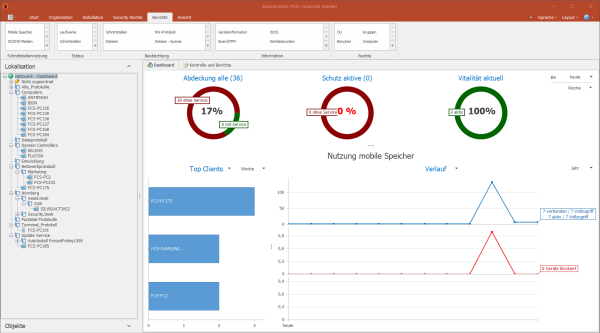
- Welche Ihrer Clients sind geschützt? Wurden verdächtige Aktionen ausgeführt? Wenn ja, wo und von wem? Das Dashboard stellt den aktuellen Status der Endpoint Security im Netzwerk grafisch dar.
- Es ermöglicht detaillierte Analysemöglichkeiten.
- Kuchen- und Balkendiagramme informieren über den Schutz-Status der Clients.
- Umfasst diverse Verläufe über die Nutzung mobiler Speicher und Dateibewegungen.
- Intuitive Drilldown-Optionen.
- Darüber hinaus verfügt es über vorgefilterte Standardberichte.
- Rechtevergabe: auf User-, Gruppen- oder Computerebene, so können jedem einzelnen Computer, Gerät, Benutzer, jeder Gruppe oder OU pro Schnittstellentyp unterschiedliche Rechte zugewiesen werden.
- Rechtehierarchie: lässt Ausnahmen von Richtlinien auf mehreren Ebenen zu.
- Individuelle Restriktionsmöglichkeiten: Schnittstellen können in jeder Hierarchiestufe mit folgenden Rechten belegt werden: alles erlaubt, nur lesen, nicht schreiben, alles verboten.
- Weitere individuelle Konfigurationsmöglichkeiten: Erlaubt z.B. die Nutzung einzelner Geräte (nach ID) oder Gerätetypen trotz Verbots.
Der Security-Dienst auf den Zielclients kann vom lokalen Administrator nicht beeinflusst oder beendet werden.
- Mit Security.Desk können auch mobilen Usern am Notebook via Code-Fernfreischaltung zeitlich begrenzte Benutzerrechte für die Schnittstellen erteilt werden, auch wenn die Notebooks vom Netzwerk getrennt sind.
- Dateien können im AES-Verfahren verschlüsselt werden.
- Bequem können eine oder mehrere Dateien über das Kontextmenü des Windows Explorers mit FCS CryptMe! ver- oder entschlüsselt werden.
- BadUSBs melden sich heimlich als Maus, Tastatur oder Netzwerkkarte am Computer an und erlauben dann eine Fernsteuerung bzw. externe Nutzung der befallenen Systeme.
- Sollte es sich um einen manipulierten USB-Stick handeln, der sich z.B. als Tastatur oder Maus ausgibt, dann kann dieser direkt vom User blockiert werden.
Zentrale Verwaltungskonsole und Agenten:
Freigabe von bestimmten Speichermedien oder auch Dateitypen blockieren und Softwareanwendungen verhindern:
Weiße Liste:
- Geräte/Gerätetypen: Die Weiße Liste erlaubt die Nutzung einzelner Geräte (nach ID) oder Gerätetypen trotz Verbots.
- Individuelle Freigaben: Sie entscheiden, ob nur ein spezielles Gerät mit Seriennummer oder ein bestimmter Gerätetyp freigegeben wird.
- Flexible Konfiguration: Weiße Listen können pro Organisationseinheit, Gruppe, Benutzer und global hinterlegt werden.
Schwarze Liste:
- Software: Die Schwarze Liste verbietet die Ausführung bestimmter Software (z.B.: Microsoft Internet Explorer).
- Dateitypen: Verbietet das Lesen/Kopieren bestimmter Dateitypen (z.B.: .doc, .jpg, .exe) von einem Wechselspeicher oder das Schreiben auf denselben.
Security.Desk als Intrusion Prevention System (IPS)
Security.Desk erkennt Angriffe auf Netzwerke und Computersysteme, kann automatische Abwehrmaßnahmen ergreifen und bietet gegenüber Firewalls zusätzlichen Schutz.
Im täglichen Einsatz legen die Administratoren über ihre zentrale Verwaltungskonsole (Security.Desk) fest, wie sich die auf den Clients laufenden Agenten verhalten sollen. Der Status der Securitydienste wird im Dashboard umfänglich aufbereitet.
USB-Sticks sind neben E-Mails und verseuchten Programmen eine der häufigsten Quellen für Schadsoftware. Doch das Risiko geht darüber hinaus: USB-Sticks können verloren gehen, wodurch dienstliche Daten leicht in die falschen Hände geraten könnten.
- Kontrolle der USB-Ports: Security.Desk überwacht und schützt vor unbefugtem Zugriff.
- Automatische Verschlüsselung: Sobald ein unverschlüsselter Stick erkannt wird, kann mit CryptMe eine Verschlüsselung durchgeführt werden.
- Sichere Entschlüsselung: Die Daten lassen sich nur mit CryptMe wieder entschlüsseln, was zusätzliche Sicherheit bietet.
- Jedem einzelnen Computer, Benutzer, jeder Gruppe oder OU können pro Schnittstellentyp unterschiedliche Rechte zugewiesen werden. Die Ebene „Jeder“ entspricht den Unternehmensrichtlinien und greift, wenn keine Ausnahmen auf höheren Hierarchieebenen definiert sind.
- Die Rechtevergabe von Security.Desk ist flexibel und ermöglicht eine klare Rechtehierarchie, die Ausnahmen auf mehreren Ebenen zulässt. Rechte der höheren Ebene übersteuern dabei die darunter liegenden Berechtigungen.
- Die Schnittstellen können in jeder Hierarchiestufe mit den folgenden Rechten konfiguriert werden:
- Alles erlaubt
- Nur lesen, nicht schreiben
- Alles verboten
- Optional kann ein Dateiprotokoll aktiviert werden, das protokolliert, wann und welche Dateien von oder auf einen Wechselspeicher kopiert wurden.
- Die Weiße Liste erlaubt die Nutzung einzelner Geräte (nach ID) oder Gerätetypen trotz bestehendem Verbot.
- Die Schwarze Liste für Software verhindert die Ausführung spezifischer Software (z.B.: Microsoft Internet Explorer).
- Die Schwarze Liste für Dateitypen blockiert das Lesen oder Kopieren bestimmter Dateitypen (z.B.: .doc, .jpg, .exe) von einem Wechselspeicher und/oder das Schreiben auf diesen. Sie kann auch invertiert werden, um nur bestimmte Dateitypen zu erlauben.
Schnittstellenüberwachung, BadUSB-Überwachung, Alerts für überwachte Schnittstellen, umfangreiches Berichtswesen, Terminal Server Dateiprotokoll, Netzwerkprotokollierung* sowie URL-Filter und Datenverschlüsselung gehören zum Leistungsumfang von Security.Desk.
* Zusatzmodul
- Proaktiv arbeitende Überwachungstechnologie durch Weiße und Schwarze Listen
- Definition der verbotenen Applikationen mittels Schwarzer Liste
- Ständige Analyse der ausgeführten Applikationen
- Die Nutzung von USB-Sticks, Modems, Bluetooth- und IrDA-Komponenten sowie Disketten und ähnlichen Geräten am Client wird überwacht.
- Die Rechtevergabe steuert, welche Zugriffsrechte Benutzer solcher Geräte haben, ob die Daten darauf verschlüsselt werden sollen und welche Dateitypen überhaupt übertragen werden dürfen.
- Zuständige Mitarbeiter sind stets darüber im Bilde, was in ihrem Netzwerk vorgeht.
- Das Monitoring erfolgt genau wie die Konfiguration über das Dashboard und über Listen der Clients und ihrem Status.
- Echtzeit-Monitoring sowie Protokoll- und Logging-Funktionen sind möglich.
- Reports gehen automatisch per Mail an die verantwortlichen Mitarbeiter und geben Aufschluss über die von jeder definierten Regel angestoßenen Aktionen.
- Filterfunktionen ermöglichen das schnelle und effiziente Durchsuchen der Protokolleinträge.
- Security.Desk kontrolliert den Einsatz von mobilen Speichern, Smartphones, Digitalkameras etc. an den PCs Ihres Netzwerkes.
- Die Software überwacht sämtliche Hardware-Schnittstellen und Internet-Protokolle (z.B. HTTP, FTP) am Endgerät.
- Active Directory-Integration.
- Rechte-Vergabe: erlauben, nur lesen, verbieten – getrennt nach HW-Schnittstelle – pro User, Gruppe, OU & Gerät.
- Protokoll von Dateibewegungen von und auf Wechseldatenträger.
- Blockierung von Lesen oder Schreiben bestimmter Dateitypen von oder auf Wechselspeicher.
- Erkennung von verbotenen „embedded files“ in Office-Dateien.
- Überwachung der Dateibewegungen lokaler Laufwerke an Thin Clients.
- Übersichtlicher zentraler Kontrollstand für Compliance Management, Dienstverteilung und Reporting.
- Freie Ergänzung zu überwachender USB-Gerätetypen.
- „Weiße Liste“ für spezielle Geräte (nach ID) oder Gerätetypen.
- Softwareanwendungen über Schwarze Liste verbieten.
- Temporäre Freischaltung von Offline-Rechnern über Zugriffscode.
- Alarm via E-Mail oder Tray Icon.
- Security-Dienst ist nicht beendbar.
- Flash Reminder – erinnert Sie beim Abmelden von Ihrem PC, falls sich am Rechner noch angeschlossene Wechseldatenträger befinden.
- Schutz vor BadUSB (Speichersticks mit manipulierter Firmware) durch die Kontrolle von Eingabegeräten (Maus und Tastatur) sowie Netzwerkadaptern.
- Pro Client werden die BIOS-Information sowie die Daten der logischen Laufwerke inklusive Kapazität (gesamt / belegt / frei) ausgelesen und angezeigt.
- Die Daten der logischen Laufwerke der Clients werden zusammen mit dem “BitLocker”-Status ausgelesen.
- Security.Desk zeigt die vollständigen Daten zum Betriebssystem der Clients an (Version, Release, Build-Nr., Service Pack etc.).
- Sie erkennen an der BIOS-Information in Security.Desk pro Gerät oder über einen Bericht, ob an diesen Clients “UEFI Secure Boot” aktiviert ist oder nicht.
- Windows Update-Optionen und Status je Rechner sowie Info zum Windows Update Server.
- Für HID Bluetooth-Geräte wie Maus und Tastatur (Human Interface Devices) wird zusätzlich der Batterie-Level an den Manager übertragen.
- Das System entfernt (entkoppelt) Bluetooth-Geräte von den Rechnern automatisch, wenn die Nutzung verboten ist.
- Integration mit Store O´Crypt (AES 256 hardwareverschlüsselter USB Stick von FCS).
Security.Desk kostenlos testen oder direkt erwerben!
Security.Desk können Sie jederzeit kostenlos testen. Gerne können Sie ein unverbindliches Angebot oder auch eine persönliche Online-Demonstration anfordern.